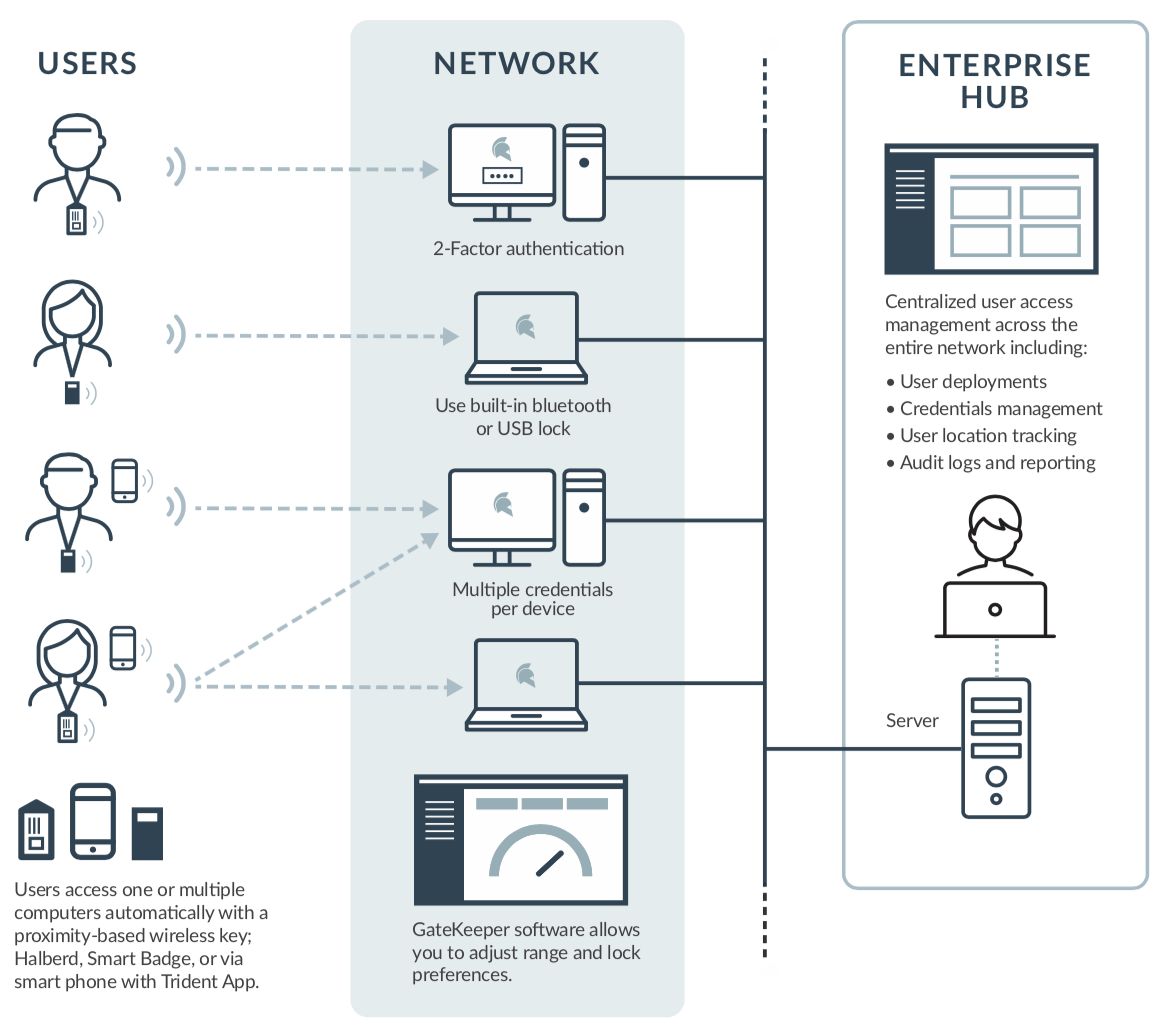
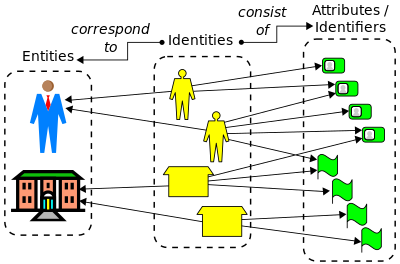
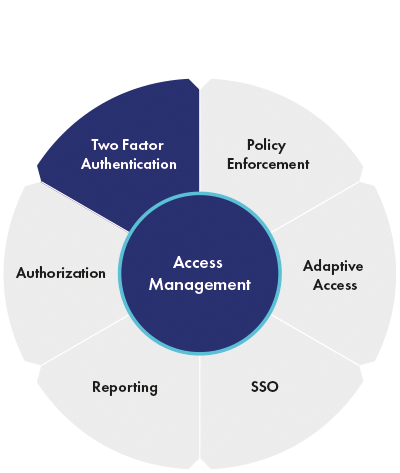
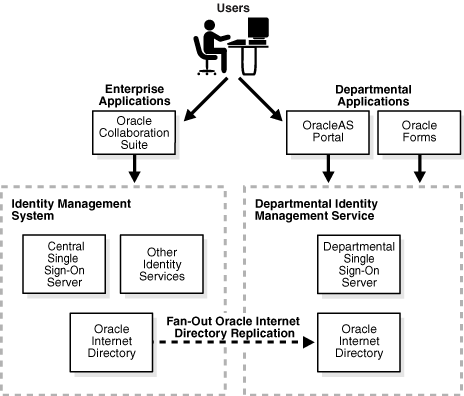
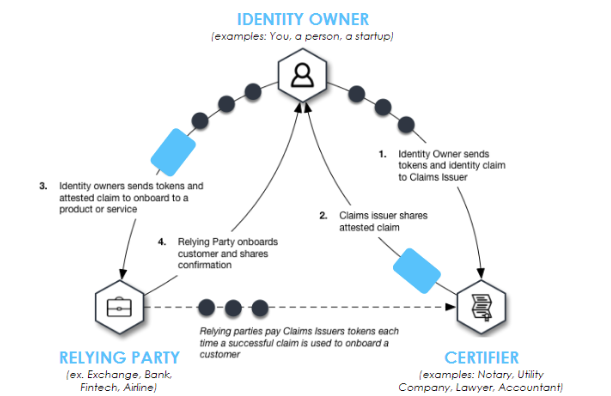
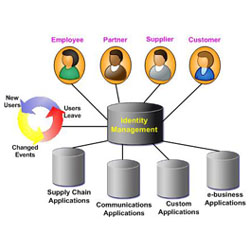
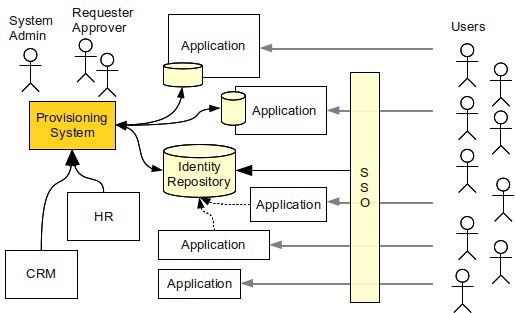
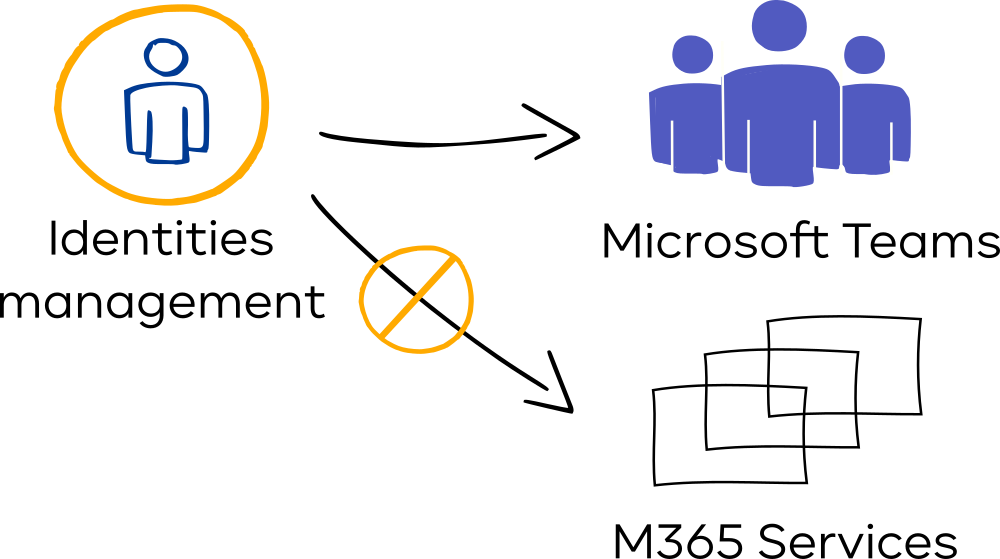
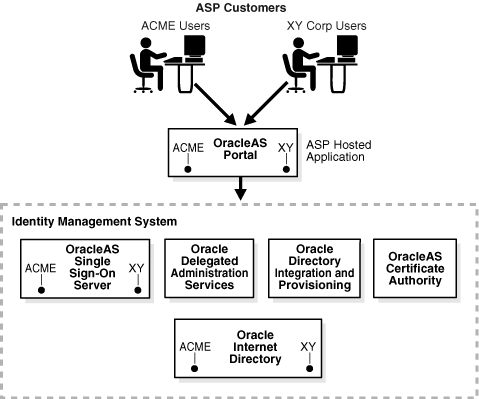
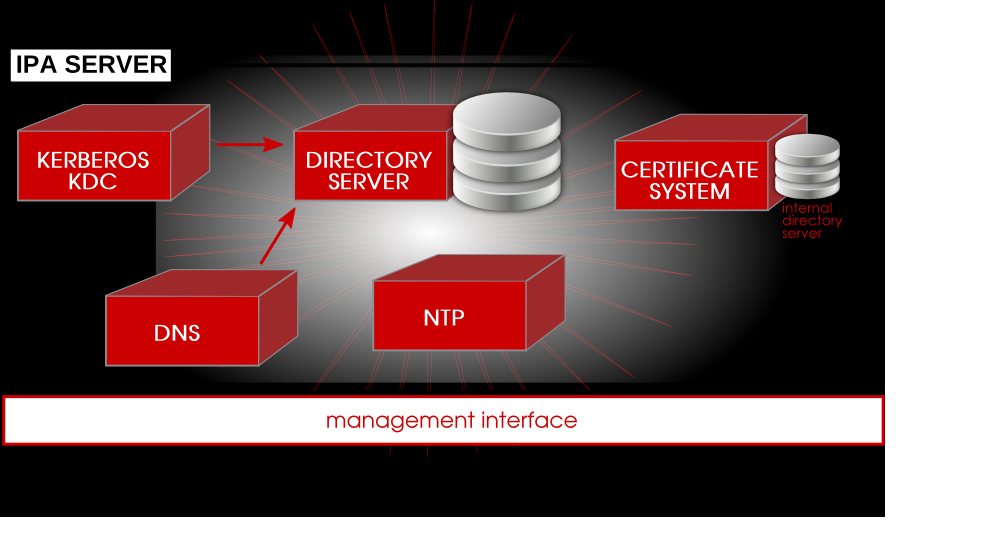
Centralized or identity and access management and decentralized identity management 7742294 Vector Art at Vecteezy

Sensors | Free Full-Text | A Smart Biometric Identity Management Framework for Personalised IoT and Cloud Computing-Based Healthcare Services

Centralized vs. Decentralized Identity Management In 2022 | by Alamira Jouman Hajjar | Fractal | Medium